First Reputation-based Blockchain Guarantees Security Against 51 Percent Attacks
Could Blockchain Ensure Integrity of Clinical Trial Data?
UIC to Lead $3M Initiative to Develop System to Identify, Patch Software Security Holes
The University of Illinois at Chicago will lead a $3 million project funded by the Defense Advanced Research Projects Agency to design, develop and evaluate a system that will identify security vulnerabilities in web software. UIC will receive $1.4 million of the funding, and the rest will support co-investigators at the University of Texas at…
Will Biotech and Pharma Be Prepared for This Year’s Cyber Threats?
Speed of Light: Toward a Future Quantum Internet
Engineering researchers have demonstrated proof-of-principle for a device that could serve as the backbone of a future quantum internet. University of Toronto Engineering professor Hoi-Kwong Lo and his collaborators have developed a prototype for a key element for all-photonic quantum repeaters, a critical step in long-distance quantum communication. A quantum internet is the “Holy Grail” of…
Cybersecurity Expert Elected Fellow of 2 Technology Organizations
Dr. Bhavani Thuraisingham, a professor of computer science at The University of Texas at Dallas and one of the world’s leading experts in data security and data mining, has been elected a fellow of two highly prestigious international technology organizations. Thuraisingham, the Louis A. Beecherl Jr. Distinguished Professor and executive director of the Cyber Security Research and…
Blockchain in Drug Discovery: Tech Could Further Collaboration, Data Sharing
Slicing Optical Beams: Cryptographic Algorithms for Quantum Networks
Army Scientists Revolutionize Cybersecurity Through Quantum Research
Scientists at the RDECOM Research Laboratory, the Army’s corporate research laboratory (ARL) have found a novel way to safeguard quantum information during transmission, opening the door for more secure and reliable communication for warfighters on the battlefield. Recent advancements of cutting-edge technologies in lasers and nanophysics, quantum optics and photonics have given researchers the necessary…
NSF Announces $78.2 Million to Support Frontiers of Cybersecurity, Privacy Research
Discovery Casts Dark Shadow on Computer Security
Researchers Close Security Vulnerability in Popular Encryption Program
World-First Program to Stop Hacking by Supercomputers
The Lattice-Based One Time Ring Signature (L2RS) enhanced security and privacy-preserving features enable large transactions and transfer of data without risk of being hacked by quantum computers and privacy revoked by unauthorised users. Monash IT experts consider L2RS as a significant leap forward in maintaining data security, user privacy and integrity for blockchain technology as…
An Ionic Black Box
While we embrace the way the Internet of Things already is making our lives more streamlined and convenient, the cybersecurity risk posed by millions of wirelessly connected gadgets, devices and appliances remains a huge concern. Even single, targeted attacks can result in major damage; when cybercriminals control and manipulate several nodes in a network, the…
Predict Responsibly: Fairness Needed in Algorithmic Decision-making
University of Toronto PhD student David Madras says many of today’s algorithms are good at making accurate predictions, but don’t know how to handle uncertainty well. If a badly calibrated algorithm makes the wrong decision, it’s usually very wrong. “A human user might understand a situation better than a computer, whether it’s information not available because it’s…
‘Design for Security’ Program Launched by Purdue, Intel
A new electronic security badge, offered through a new collaboration between Intel Corp. and Purdue University, will emphasize using secure design principles throughout the product development life cycle. The “Design for Security” badge will be based on a series of courses offered on Purdue’s campus and also online beginning in the fall of 2018. The…
Cybersecurity’s Next Major Challenge: Connecting Human and Machine Intelligence
HADES Creates Alternate Reality to Mislead Hackers
The Russian novelist Fyodor Dostoevsky once postulated that the devil no longer uses fire and brimstone but instead simply tells you what you want to hear. Sandia National Laboratories cyber researchers go with that second option when it comes to foiling a hacker. Rather than simply blocking a discovered intruder, Vince Urias, Will Stout and…
Berkeley Lab Aims to Strengthen Cybersecurity of the Grid
As the U.S. electricity grid continues to modernize, it will mean things like better reliability and resilience, lower environmental impacts, greater integration of renewable energy, as well as new computing and communications technologies to monitor and manage the increasing number of devices that connect to the grid. However, that enhanced connectivity for grid operators and…
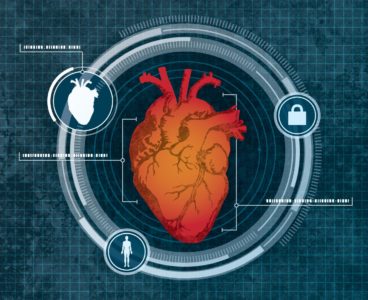
Goodbye, Login. Hello, Heart Scan
Forget fingerprint computer identification or retinal scanning. A University at Buffalo-led team has developed a computer security system using the dimensions of your heart as your identifier. The system uses low-level Doppler radar to measure your heart, and then continually monitors your heart to make sure no one else has stepped in to run your…
‘The Dark Side’ of Quantum Computers
Ultra-small Nanocavity Advances Technology for Secure Quantum-Based Data Encryption
Researchers have developed a new type of light-enhancing optical cavity that is only 200 nanometers tall and 100 nanometers across. Their new nanoscale system represents a step toward brighter single-photon sources, which could help propel quantum-based encryption and a truly secure and future-proofed network. Quantum encryption techniques, which are seen as likely to be central…
Innovative Technique to Curtail Illegal Copying of Digital Media
In today’s digital world it can be challenging to prevent photos, videos and books from being illegally copied and distributed. A new light-based technique is making it more practical to create secure, invisible watermarks that can be used to detect and prosecute counterfeiting. “In our research, we use a complex pattern of light, or diffraction…
Greater Privacy, Security Measures Needed to Protect Patient Info in Mobile Health Tech
With over two-thirds of U.S. adults owning asmartphone, and the rise in miniaturized sensors and low-power body area networks that are used for remote health monitoring, mobile health (mHealth) is beginning to experience a boom. While the technology has the potential to increase healthcare quality, expand access to services, reduce costs, and improve personal wellness…