Researchers anticipate a large network of EV charging equipment to be an attractive target for adversaries or criminal enterprises. Idaho National Laboratory’s Cerberus system — relying on basic sensors and computer hardware linked together in a smart configuration — sharply limits or sometimes eliminates damage to assets and human health. Recent work demonstrated that high-power…
University-based cybersecurity centers receive $15 Million for research and training
From the DOE: The U.S. Department of Energy (DOE) announced $15 million in funding to establish six university-based electric power cybersecurity centers that will foster collaborations across the energy sector to address gaps in energy security research and provide cybersecurity education programs. Each university, selected by the DOE’s Office of Cybersecurity, Energy Security, and Emergency…
U.S. DOE launches digitizing utilities prize for grid reliability and resilience solutions
The U.S. Department of Energy’s (DOE) Office of Electricity (OE) has launched the $1.85 million Digitizing Utilities Prize Round 2. This competition aims to connect electric utilities with interdisciplinary teams of software developers and data experts to transform digital systems and data analytics for utilities in the energy sector. This round will also award prizes…
R&D 100 winner of the day: Intelligence-Driven Cybersecurity Analytic Platform
Ransomware has ravaged industries all around the world in recent years, no matter if it is manufacturing, technology, or public infrastructure. According to forecasting by cyber research firm Cybersecurity Ventures, ransomware attacks will be launched every 2 seconds on average in 2031 and will cause a global loss of $7.3 trillion. The outbreak of COVID-19…
R&D 100 winner of the day: MOSAICS: Bringing the Future of Industrial Cybersecurity Into Focus
Developer: Johns Hopkins University Applied Physics Laboratory Co-developers: Sandia National Laboratories, Idaho National Laboratory, Pacific Northwest National Laboratory The vulnerability of industrial control systems (ICS) to cyberattacks has become alarmingly clear in the past several years, with a series of headline-grabbing hacks. In response, the Johns Hopkins Applied Physics Laboratory (APL), in partnership with Sandia…
R&D 100 winner of the day: Plug-N-Play Appliance for Resilient Response of Operational Technologies (PARROT)
The Plug-N-Play Appliance for Resilient Response of Operational Technologies (PARROT), developed by Idaho National Laboratory, provides an extra layer of security from cyberattacks on critical infrastructure operations. When placed between control systems and infrastructure, PARROT isolates a cyberattack, provides a manual or automated response, and prevents harmful impacts while maintaining operations. Most critical infrastructure in…
BIO-ISAC formed to protect bioeconomy infrastructure from increasing attacks
Dotmatics, a scientific informatics software and services company that is helping to automate laboratory data workflows for scientific discovery and innovation research, has announced that Charles Fracchia, VP of Data and founder of BioBright, a Dotmatics company, has been appointed to the Bioeconomy Information Sharing and Analysis Center (BIO-ISAC) Board of Directors and the Executive…
U.S. Army’s Sentinel A4 radar program receives Orolia M-Code solution
In September 2019, Lockheed Martin was awarded a contract to develop the U.S. Army’s Sentinel A4 system, an air and missile defense radar that will provide improved capability against dynamic threats. The following November, Orolia Defense & Security announced the availability of M-Code Military GPS receivers in its flagship SecureSync – the first Defense Information…
NUS researchers bring attack-proof quantum communication two steps forward
by National University of Singapore Quantum key distribution (QKD) is a method for secure communication that uses quantum mechanics to encrypt information. While the security of QKD is unbreakable in principle, if it is incorrectly implemented, vital information could still be stolen by attackers. These are known as side-channel attacks, where the attackers exploit weaknesses…
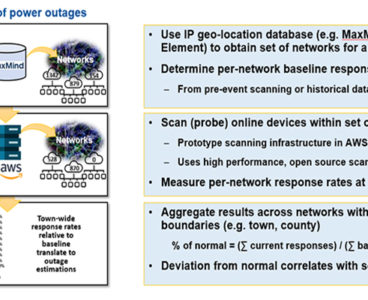
R&D 100 winner of the day: CyberPow: Cyber Sensing for Power Outage Detection
MIT Lincoln Laboratory’s CyberPow: Cyber Sensing for Power Outage Detection uses pervasive, internet-connected devices as an alternative sensing network to rapidly estimate and map the extent and location of power outages across geographic boundaries. Enabling real-time situational awareness without the need for electric utilities, allowing more timely and effective post-disaster decision making and resource prioritization.…
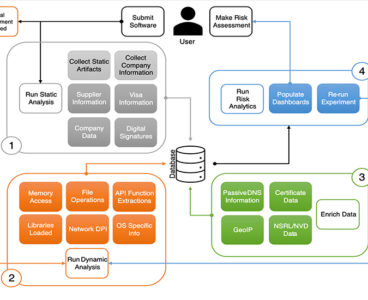
R&D 100 winner of the day: High-density Evaluator of COTS Applications for Trust and Efficacy (HECATE)
Recent advances in adversary sophistication have led to targeting the software supply chain to inject malicious code into trusted software applications, subverting visibility to developers and users alike. As Hecate was a protector in Greek mythology, such is Sandia’s HECATE platform, protecting organizations by assessing the risk of commercial-off-the-shelf (COTS) applications before they hit the…
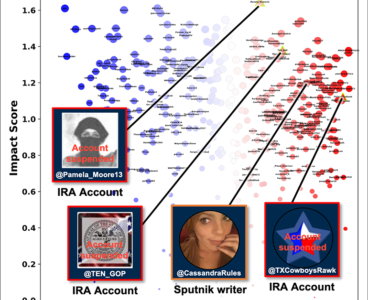
R&D 100 winner of the day: Reconnaissance of Influence Operations (RIO)
Hostile influence operations that exploit digital communications and social media pose a rising threat to open democracies. MIT Lincoln Laboratory’s Reconnaissance of Influence Operations (RIO) allows early indication of influence operation campaigns and has the potential to forecast effects of targeted counter responses. This end-to-end system framework collects contextually relevant data, identifies potential influence operation…
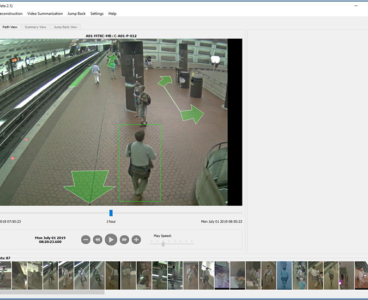
R&D 100 winner of the day: FOVEA (Forensic Video Exploitation and Analysis) Tool Suite
The FOVEA tool suite, from MIT Lincoln Laboratory, addresses a major capability gap in video surveillance systems: efficient forensic review and investigation. Once integrated with a video management system, the analytics can be applied to any camera feed without any additional hardware or need for preprocessing the video data. FOVEA acts as a force-multiplier for…
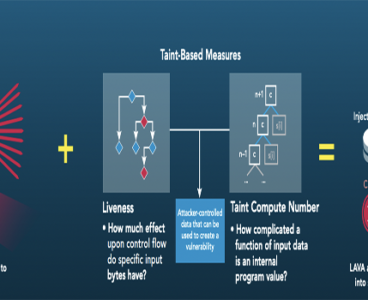
R&D winner of the day: LAVA: Large-Scale Vulnerability Addition
Work on automating software vulnerability discovery has long been hampered by a shortage of ground truth corpora with which to evaluate tools and techniques. This lack of ground truth prevents authors and users of tools from being able to measure fundamental quantities such as the miss and false alarm rates of bug-finding systems. Large-scale Automated…
R&D 100 winner of day: Timely Randomization Applied to Commodity Executables at Runtime (TRACER)
Sophisticated, modern cyberattacks that hijack the control of a machine remotely heavily rely on the static and homogeneous nature of computer systems. Researchers at MIT Lincoln Laboratory developed Timely Randomization Applied to Commodity Executables at Runtime (TRACER), a patented technology to prevent such attacks in closed-source commodity applications running on top of Windows operating system…
SwRI hacks electric vehicle charging to demonstrate cybersecurity vulnerabilities
Engineers at Southwest Research Institute were able to interfere with the charging process of an electric vehicle (EV) by simulating a malicious attack as part of an automotive cybersecurity research initiative. The SwRI team reverse-engineered the signals and circuits on an EV and a J1772 charger, the most common interface for managing EV charging in…
R&D 100 winner of the day: CoDeAc
Speed is of the essence in radiological response to prevent the spread of contamination. CoDeAc, from Idaho National Laboratory, allows crucial decisions to be made quickly during an event. The CoDeAc pack has no equal in the rapid detection of actinides and is capable of on-site deployment, making it the go-to tool for first responders…
R&D 100 winner of the day: PBI: Public Biometric Infrastructure
Hitachi’s PBI: Public Biometric Infrastructure is the world’s first biometric authentication system that does not store any biometric data such as facial and finger-vein features anywhere, minimizing the risk of data leakage and abuse. It processes empty-handed payments and bank transactions without a card or smartphone while strongly protecting security and privacy. It runs on…
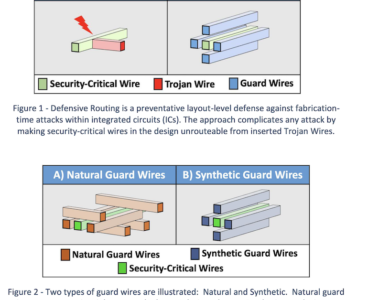
R&D 100 winner of the day: Defensive Wire Routing for Untrusted Integrated Circuit Fabrication
With increased performance from smaller transistors, U.S. Government access to trusted high-performance foundries is decreasing, thereby disadvantaging U.S. military systems which require high degrees of trust. One concern with untrusted fabrication is the issue of malicious modification or tamper, where a trusted design is modified by a fabricator to insert a “hardware Trojan” or “backdoor”…
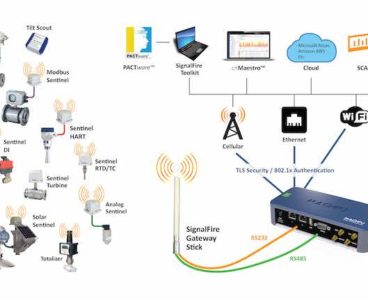
SignalFire Wireless Telemetry and Machfu introduce an integrated 900MHz sensor network-to-cloud solution
SignalFire Wireless Telemetry, a manufacturer of industrial wireless telemetry products, and Machfu, a provider of industrial IoT solutions, announce the integration of SignalFire’s wireless sensor network with Machfu’s Industrial IoT Gateway. The Machfu IIoT Gateway incorporates edge intelligence, multi-protocol translation capabilities and multi-dimensional security features, resulting in a versatile and secure sensor-to-cloud solution. Operating the…
R&D 100 winner of the day: Matter-wave modulating secure quantum communicator (MMQ-Com)
The Information Age we live in demands data security, but the safety of our data is in peril given the rise of quantum computers that can decode classical encryption schemes. Currently, the only safe alternatives are quantum cryptography approaches that rely on photons. With Berkeley Lab’s Matter-wave modulating secure quantum communicator (MMQ-Com) innovation, the world…
Addressing the fast-changing challenges of cybersecurity
What scientists and engineers need to know to help keep software, hardware and connected systems secure By Patricia Panchak, Contributing Writer In the cat-and-mouse struggle against bad actors in our inter-networked world, scientists and engineers are on the front lines. As developers of technology that can mean the difference between an adversarial breach and a…
Keeping an eye on China is more important than ever
By about 2025, China will likely surpass the U.S. for the first time ever in the amount of dollars spent on R&D. Earlier this year, I had the opportunity to sit down with Rep. Chrissy Houlahan, a first-term congresswoman from southeastern Pennsylvania (and an industrial engineer), who sits on the House Committee on Foreign Affairs’…
Mixed-signal hardware security thwarts powerful electromagnetic attacks
Purdue innovators are at Silicon Valley’s premier chip-design conference to unveil technology that is 100 times more resilient to electromagnetic attacks to secure Internet of Things devices. Security of embedded devices is essential in today’s internet-connected world. Security is typically guaranteed mathematically using a small secret key to encrypt the private messages. When these computationally…
Intrusion alert: System uses machine-learning, curiosity-driven ‘honeypots’ to stop cyber attackers
In recent months, the FBI issued a high-impact cybersecurity warning in response to increasing attacks on government targets. Government officials have warned major cities that such hacks are a disturbing trend that is likely to continue. A new tool from Purdue University researchers may help stop some of those threats. The Purdue team created a…